It surprises me how numerous individuals confuse the significance of susceptability scanning with penetration testing. Vulnerability scanning can not replace the significance of infiltration screening, as well as infiltration screening, by itself, can not secure the entire network. Both are necessary at their respective degrees, required in cyber threat evaluation, and also are called for by criteria such as PCI, HIPPA, ISO 27001, etc.
Either penetration testing or vulnerability scanning depends mainly on 3 variables: Range, Threat and also Criticality of assets,and Expense and also Time. Infiltration screening range is targeted as well as there is always a human element included. There is no automated penetration testing point. Penetration testing requires making use of tools, often a great deal of tools.
Website Vulnerability Scanner
A great penetration tester always at some time throughout their screening craft a script, adjustment parameters of an assault or tweak setups of the devices he or she may be utilizing. It might be at application or network level yet specific to a feature, division or variety of properties. One can include whole framework and also all applications yet that is not practical in the actual world because of price as well as time.
Investing a great deal of money on low-risk properties which might take a variety of days to exploit is not useful. Infiltration screening calls for high knowledgeable knowledge which's why it is costly. Infiltration testers often make use of a brand-new vulnerability or uncover susceptabilities that are not known to normal organization processes.
The Ultimate Guide To Vulnerability Scanning
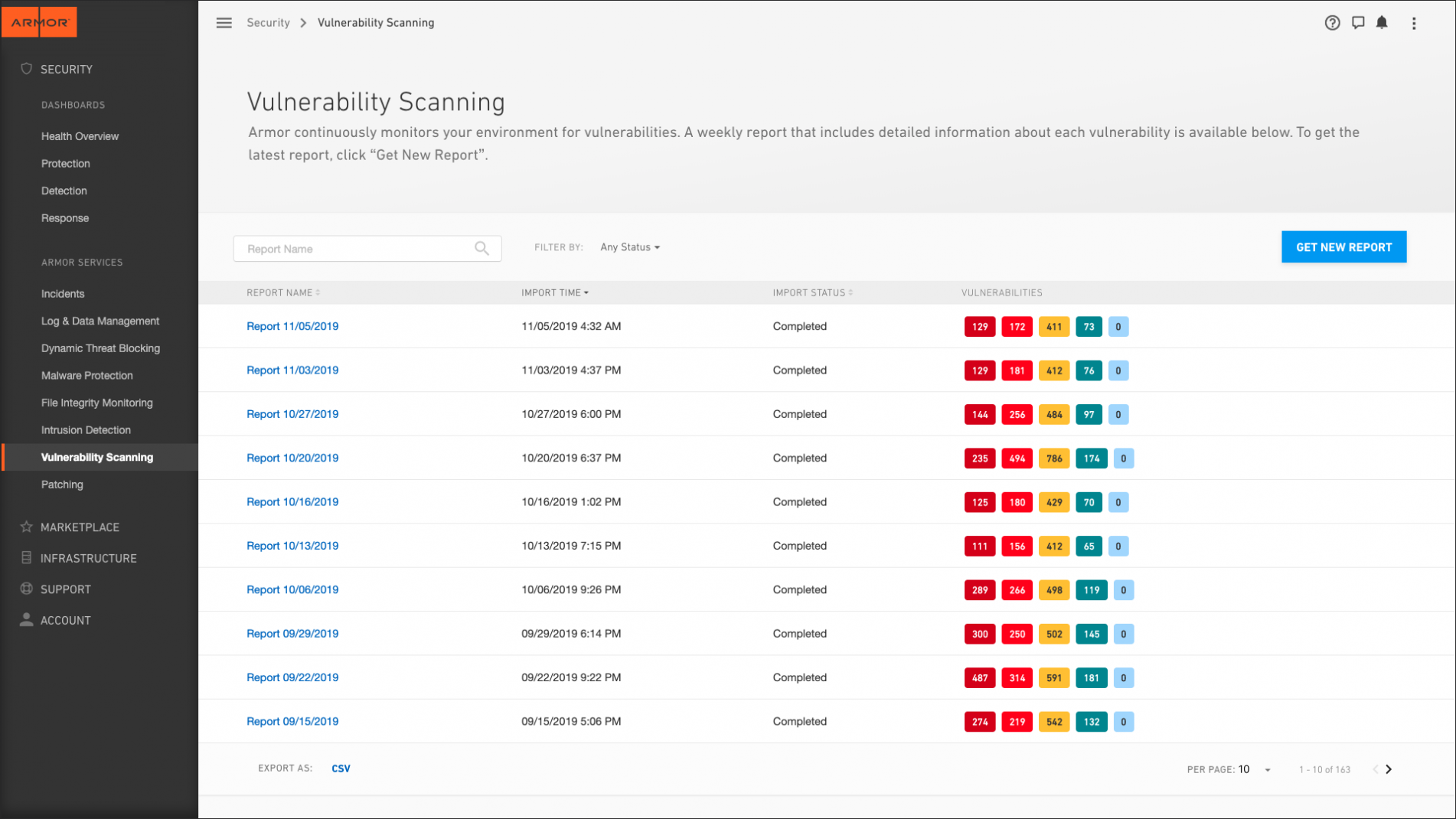
It is typically performed yearly and also records are brief and also to the factor. Infiltration screening does have a more than typical possibility of creating blackouts. On the various other hand, vulnerability scanning is the act of recognizing prospective vulnerabilities in network gadgets such as firewalls, routers, buttons, web servers as well as applications.
It does not make use of the vulnerabilities. Vulnerability scanners simply identify possible vulnerabilities; they do not manipulate the susceptabilities. Therefore, they are not developed to find zero-day ventures. Susceptability scanning scope is business-wide as well as calls for automated tools to handle a high number of properties. It is wider in range than penetration screening.
Vulnerability Scanning 101
It is typically run by managers or a safety and security personal with excellent networking knowledge. Vulnerability scans can be run frequently on any number of possessions to determine well-known vulnerabilities are discovered and also covered. Thus, you can get rid of a lot more severe susceptabilities for your useful sources swiftly. A reliable means to remediate susceptabilities is to comply with the vulnerability monitoring lifecycle.
Susceptability monitoring can be fed right into patch administration for efficient patching. Great post to readPatches needs to be examined on a test system before presenting to manufacturing. Safety regulates & requirements highlight the significance of susceptability scanning. For instance, The Center for Internet Protection (CIS) Control # 3, "Continual Susceptability Management," calls on safety professionals to "Continuously acquire, evaluate, as well as take activity on brand-new info in order to identify susceptabilities, remediate, and minimize the window of chance for attackers".
Vulnerability Management Process
It states that you need to "Run inner and also exterior network vulnerability scans a minimum of quarterly and after any type of significant change in the network." Both vulnerability scanning and penetration screening can feed right into the cyber danger analysis procedure and help to identify controls best suited for the company, division or a method.
It is very important to recognize the distinction; each is very important and has different functions as well as end results. Training is additionally important as providing a device( s) to your safety personnel does not imply that the environment is safe. Absence of knowledge in operation a device( s) properly poses a bigger safety and security threat.
Vulnerability Management Services
Vulnerability scanners are automated tools that permit organizations to check if their networks, systems and also applications have safety weak points that might expose them to attacks. Vulnerability scanning is a common technique throughout business networks and also is frequently mandated by sector criteria and also government policies to enhance the company's safety posture.
Susceptability scans can be carried out from outdoors or inside the network or the network sector that's being examined. Organizations can run exterior scans from outside their network border to identify the exposure to assaults of web servers as well as applications that come directly from the net. On the other hand, interior susceptability scans purpose to identify flaws that hackers can manipulate to move side to side to different systems and also servers if they access to the neighborhood network.
Best Network Vulnerability Scanning Software
Due to the fact that of this, any type of susceptability administration program ought to start with a mapping and supply of a company's systems and also a category of their value based on the accessibility they provide and the information they hold. Some industry criteria, such as the Payment Card Industry Data Protection Requirement (PCI-DSS), require organizations to carry out both external as well as interior vulnerability scans quarterly, along with every single time new systems or parts are installed, the network geography modifications, the firewall program regulations are customized, or various software program products are updated.
With the prevalent fostering of cloud-based infrastructure recently, susceptability scanning procedures need to be adapted to consist of cloud-hosted properties as well. External scans are specifically vital in this context because misconfigured as well as unconfident implementations of data sources as well as various other services in the cloud have actually been an usual event. Susceptability scanning should be enhanced with infiltration testing.
Vulnerability Scanner
Susceptability scanning is an automatic activity that depends on a data source of known vulnerabilities such as CVE/NVD-- scanning vendors maintain more complete databases-- however does not typically include the exploitation of recognized defects. At the same time, penetration screening is a much more involved process that consists of manual penetrating and exploitation by a security expert in simulate what a real enemy would certainly do.
Vulnerability scans can be confirmed as well as unauthenticated, or credentialed and also non-credentialed. The non-credentialed scans uncover solutions that are open on a computer over the network and send packages on their open ports to identify the version of the os, the version of the software program behind those solutions, if there are open file shares, as well as other info that is offered without verifying.